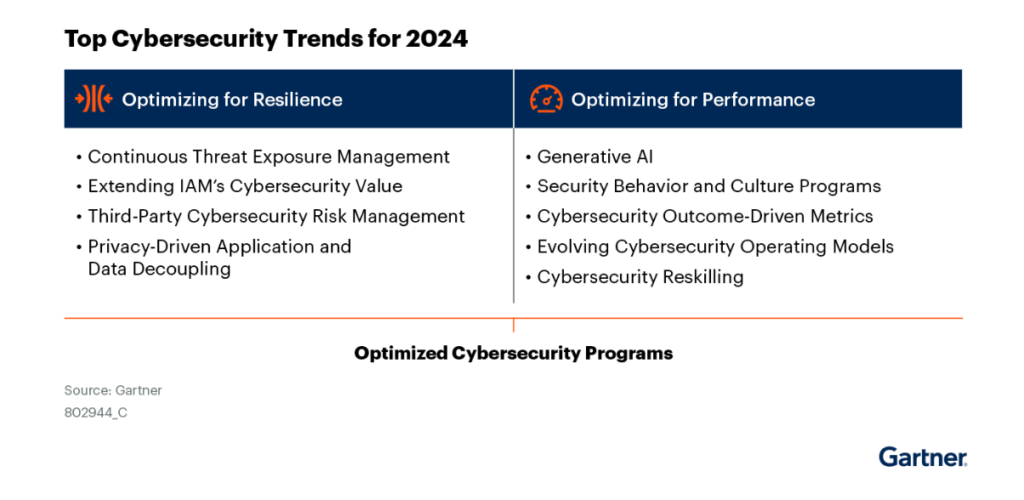
Security and risk management leaders face disruptions on multiple fronts: technological, organizational, and human. Preparation and pragmatic execution are vital to address these disruptions and deliver an effective cybersecurity program.
What lies ahead for cybersecurity leaders?
Opportunities:
- Security and risk management (SRM) leaders can improve the security function’s reputation and performance by using generative artificial intelligence (GenAI) in proactive collaboration with business stakeholders. This will help lay the foundations for ethical, safe and secure use of this disruptive technology.
- Investment in effective risk management of third-party services and software, enhanced security for the identity fabric, and continuous monitoring of hybrid digital environments can harden an organization’s attack surface and strengthen its resilience.
- Aligning security governance efforts with the use of business-aligned cybersecurity reporting can improve the security function’s performance and reputation as a trusted partner and key enabler of an organization’s strategic objectives.
- Increased focus on the human elements of security programs continues to show significant promise in the mission to minimize the impact of employees’ insecure behavior. It can also provide greater assurance when experimenting with emerging technologies in democratized digital environments.